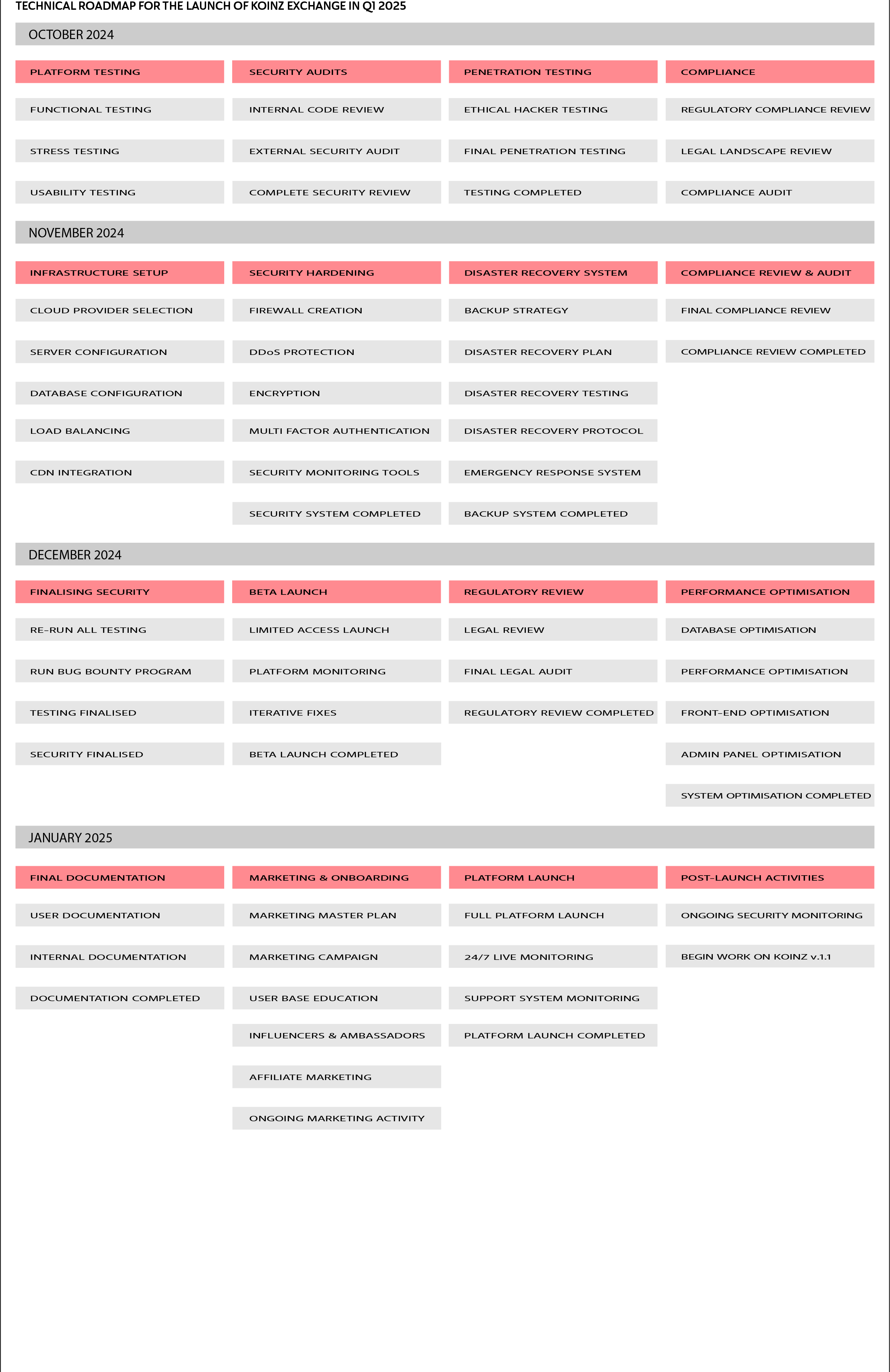
Technical Roadmap for Koinz Launch
Month 1: Finalize Testing and Security Audits
Complete Testing on Testnet
Functional Testing: Ensure all core functionalities are working as expected under various scenarios.
Stress Testing: Simulate high-load conditions to verify system stability and performance.
Usability Testing: Validate user experience with both seasoned and novice users to ensure intuitive navigation.
Security Audits
Internal Code Review: Conduct an in-depth review of the source code by internal security experts to identify potential vulnerabilities.
External Security Audit: Engage a reputable third-party security firm to perform a comprehensive audit, focusing on:
Smart contract security (if applicable).
User authentication mechanisms.
Data encryption.
Network security and DDoS attack mitigation strategies.
Penetration Testing
Hire Ethical Hackers: Contract a team of ethical hackers to perform penetration testing, simulating various attack vectors.
Address Vulnerabilities: Prioritize fixing any identified vulnerabilities immediately, re-test after fixes.
Finalize Compliance Requirements
Regulatory Compliance: Ensure adherence to all applicable local and international regulations.
Legal Review: Engage with legal counsel to confirm the platform’s compliance with relevant financial and data protection laws.
Month 2: Infrastructure Setup and Security Hardening
Infrastructure Deployment
Production Environment Setup:
Cloud Provider Selection: Choose a reliable cloud provider with robust security features (e.g., AWS, Google Cloud, Azure).
Server Configuration: Deploy high-performance servers with auto-scaling capabilities to handle varying traffic loads.
Database Setup: Use a distributed database architecture to ensure high availability and redundancy.
Load Balancing: Implement load balancers to evenly distribute traffic and avoid single points of failure.
CDN Integration: Use a Content Delivery Network (CDN) to enhance website speed and reliability.
Security Hardening
Firewall Configuration: Set up advanced firewalls to protect against unauthorized access.
DDoS Protection: Implement anti-DDoS measures, including traffic filtering and rate limiting.
Encryption:
SSL/TLS: Ensure all data transmission is encrypted using SSL/TLS protocols.
Database Encryption: Encrypt sensitive data at rest using strong encryption algorithms.
Multi-Factor Authentication (MFA): Require MFA for all administrative access to the platform.
Security Monitoring Tools: Set up real-time monitoring tools for detecting and responding to suspicious activities.
Disaster Recovery Planning
Backup Strategy: Implement a comprehensive backup strategy, including daily backups of critical data and weekly full system backups.
Disaster Recovery Testing: Conduct tests to ensure the disaster recovery plan works effectively.
Month 3: Final Preparations and Beta Launch
Final Security Checks
Re-run Penetration Tests: Perform another round of penetration testing to ensure all previously identified vulnerabilities have been resolved.
Conduct a Bug Bounty Program: Launch a bug bounty program to incentivize external security experts to find any remaining vulnerabilities.
Beta Launch
Limited Access Launch: Open the platform to a select group of users (invite-only) to gather real-world usage data.
Monitor and Analyze: Closely monitor system performance, user feedback, and any security alerts.
Iterative Fixes: Address any issues found during the beta phase immediately, deploying patches as necessary.
Final Regulatory Review
Ensure Compliance: Re-validate compliance with regulatory requirements based on feedback from the beta phase and any changes made.
Performance Optimization
Database Optimization: Fine-tune database queries and indexes for maximum performance.
Front-End Optimization: Ensure the front-end is optimized for speed and responsiveness.
Month 4: Final Launch Preparation and Full Deployment
Finalize Documentation
User Documentation: Prepare comprehensive guides for users, including FAQs, troubleshooting, and tutorials.
Internal Documentation: Ensure all internal processes, deployment scripts, and recovery procedures are thoroughly documented.
Marketing and User On-boarding
Launch Marketing Campaign: Roll out a marketing campaign to build anticipation and attract users.
User Education: Provide educational resources on how to use the platform safely, focusing on security best practices.
Full Platform Launch
Go-Live: Transition from the beta phase to full production launch, making the platform accessible to the public.
24/7 Monitoring: Ensure round-the-clock monitoring of the platform to detect and respond to any issues immediately.
Support Team Readiness: Ensure the customer support team is fully trained and ready to handle any user issues.
Post-Launch Activities
Ongoing Security Monitoring: Continue real-time monitoring and conduct regular security audits.
Performance Scaling: Scale infrastructure as user base grows, ensuring consistent performance.
Continuous Improvement: Gather user feedback, identify areas for improvement, and roll out updates and new features accordingly.
Best Practices
Security First: Prioritize security at every step, ensuring all data, transactions, and communications are secure.
Continuous Testing: Regularly test the platform, especially after making changes, to ensure stability and security.
Scalability: Design the infrastructure to scale efficiently with the growing user base.
Compliance: Stay updated on regulatory changes and ensure ongoing compliance.
User-Centric Design: Focus on providing a seamless, intuitive user experience.
Transparent Communication: Keep users informed about platform status, updates, and any potential issues.
